b01lers CTF 2024 | CTF WriteUp | Misc | Bash Jail
Category: Misc
1)wabash
wabash, its a river, but also a new shell! Flag is in /flag.txt
nc gold.b01le.rs 7004
Description
It is a bash jail through which we must bypass the filtering techniques to execute our command.
Solution:
Let's check the given nc address.
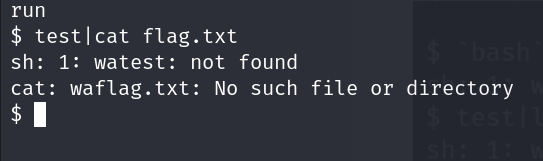
It has given an input by itself which is bash.But the command was executed as wabash which means a "wa" is getting appended before the command.
Let's pipe and send a command
Now the ls command works.We got the output as run.It was given that our flag is in /flag.txt.Let's cat it.
We can see that 'wa' is prepended to each word after the line is split by space.So we cannot give any command with spaces.
That's where the Internal Field Separator(IFS) comes in linux. IFS defaults to a space, tab, and newline character.So we could use it instead of directly giving space.
|cat${IFS}/flag.txt
It worked and we got the flag.
bctf{wabash:_command_not_found521065b339eb59a71c06a0dec824cd55}
2)misc/bash cat with pipe
My terminal seems to be stuck... please help me fix it!
nc gold.b01le.rs 7002
Description
The task is to find the flag and read it by bypassing filtering techniques.
Solutions:
Let's visit the given address and check who is there?
We can see that the program is stuck after the pipe.Lets give ls.
Three files are given and we are interested in the flag.txt.
Let's cat it out.
Oops.... The text flag is not allowed as input.
So what shall we do?
We could list(ls) the files and give those as arguments to cat by using xargs.
ls|xargs cat
All the files in the folder will get printed.Since flag.txt is the first it gets printed first so scroll up and we will get the flag.
bctf{owwwww_th4t_hurt}
Keep Learning....
Happy Hacking!!!!!







Comments
Post a Comment