UNbreakable International 2024 - Team | CTF Writeup | Network
1)just-an-upload
Category: Network
The team captured this traffic. Can you find what's in there ?
DESCRIPTION
The task is to inspect the network traffic packets and figure out whether any files are being uploaded. Then we extract a zip file from wireshark.
Solution
We are given a pcap file osc.pcapng .
Let’s fire up wireshark and open the file.Upon opening the file, we are given a huge list of packets captured.
First things first, usually the challenges are based on http traffic . So filter out the packets by searching http in the display filter on top.
Now the http packets are displayed.

We can see that there is a POST request to /upload.php location which is uploading a zip file. Lets check what is being uploaded.
Right click on the packet . Select Follow —> HTTP STREAM .
Now we can see the whole http stream where the zip file is being uploaded.
In this window we can see a flag.txt text in the content of body. It looks like there is file named flag.txt which is being zip compressed. Lets extract the content to get the zip file.
To extract a zip file from wireshark:
1)Select the packet stream to be extracted
-
Click File —> Export Objects —> HTTP
-
Select the packet that contains zip file.
4) Click Save.
The contents of the extracted file is:
Now the content has been saved as upload.php .We need to extract only the zip file parts.
To do that:
- Open wxHexEditor
You can download the tool from here: Download Link
- Open the upload.php file
3)Select the blue marked hex till 0D 0A hex. 50 4B should be the first hex after the deletion. It is the signature bytes of zip file
4) Now we have to remove the unwanted stuff at the end of the file. Remove the blue marked hexes.
5)Save the file as new.zip
Now we have the zip file, time to uncompress it. Go to the folder where the zip file is saved. Then,
unzip new.zip
A file called flag.txt is extracted now.
cat flag.txt and scroll up, There lies the flag.
ctf{F1l3_Upl04d_T0_C2_S3rv3r}
2)sums-up
Category: Network
SOC analysts saw some strange DNS traffic. Wanted you to figure out what was exfiltated , can you check it and sum it up ?
Objective:
To analyze a network traffic file and use the hint in bold characters to extract checksum of each DNS packets to get the flag.
SOLUTION
We are again given a pcap file malicious_sums.pcap
Open the file with wireshark.
We can see a lot of DNS packets.
Click on a packet and check its headers.
In the DESCRIPTION, a few words are marked in bold.(check,sum it up).
It looks like a hint.Let’s see if there is any header with those words.
Yes there is. It is called checksum.
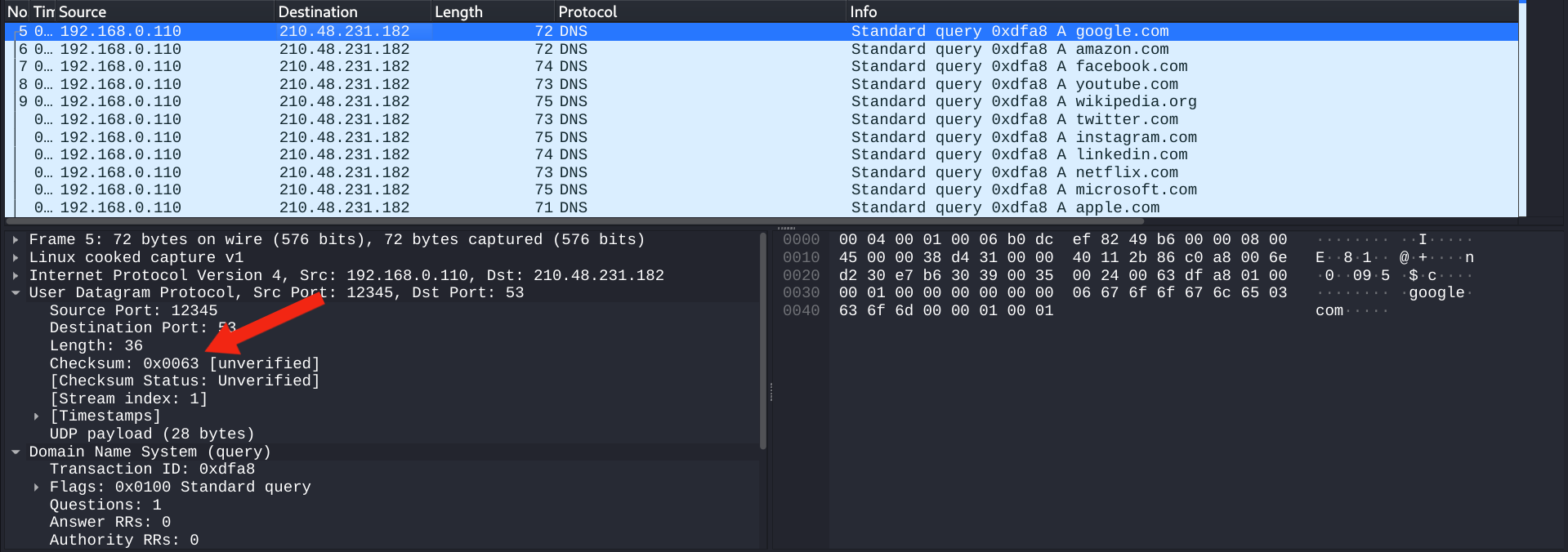
Checksum has a value of 0x63.Let’s check what is that in ASCII.
It is c. We know that the flag starts with ‘c’. Now we need to check the checksum of each packet and convert it from hex to ascii to get the whole flag.
Full hex:
6374667b3463705f346e645f3464705f636833636b73756d355f3472335f3376316c5f7072303076335f6d335f7772306e675f6a68756e6964727d
When converted to ASCII, We get the Flag:
ctf{4cp_4nd_4dp_ch3cksum5_4r3_3v1l_pr00v3_m3_wr0ng_jhunidr}
Keep Learning......
Happy Hacking!!!!!








Comments
Post a Comment